Description: Nagini is the 2nd VM of 3-box HarryPotter VM series in which you need to find 3 horcruxes hidden inside the machine (total 8 horcruxes hidden across 3 VMs of the HarryPotter Series) and ultimately defeat Voldemort.
Difficulty: medium
信息收集
|
|
结果
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 48:df:48:37:25:94:c4:74:6b:2c:62:73:bf:b4:9f:a9 (RSA)
| 256 1e:34:18:17:5e:17:95:8f:70:2f:80:a6:d5:b4:17:3e (ECDSA)
|_ 256 3e:79:5f:55:55:3b:12:75:96:b4:3e:e3:83:7a:54:94 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Site doesn't have a title (text/html).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
ssh爆破依旧失败
渗透过程
SSRF打mysql
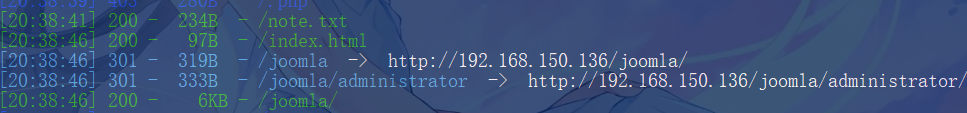
扫目录
|
|
结果
note.txt
Hello developers!!
I will be using our new HTTP3 Server at https://quic.nagini.hogwarts for further communications.
All developers are requested to visit the server regularly for checking latest announcements.
Regards,
site_amdin
发现joomla,继续扫
|
|
扫出来是个joomla站点且存在文件泄露
web.config.txt、configuration.php.bak等
扫joomla的过程中可以看看先扫出来的note.txt,需要使用HTTP3访问https://quic.nagini.hogwarts,在hosts中添置一下,吐了,quiche装不上。。。快进到成功访问获得文件internalResourceFeTcher.php和上面已经扫到的configuration.php.bak。internalResourceFeTcher.php存在SSRF,可以通过file任意文件读,公钥没读到,想起来备份文件中有日志文件地址,读一下试试,还是啥都读不到emmm
回去重新看备份文件,发现有数据库配置
public $host = 'localhost';
public $user = 'goblin';
public $password = '';
public $db = 'joomla';
public $dbprefix = 'joomla_';
开启了无密码登录,那我们就可以通过SSRF进行数据库操作,使用工具 Gopherus生成payload(第一次可能不会成功,刷新几次页面就有了)
|
|
获得管理员信息
site_admin site_admin@nagini.hogwarts $2y$10$cmQ.akn2au104AhR4.YJBOC5W13gyV21D/bkoTmbWWqFWjzEW7vay
密码爆破不出来,只能通过修改密码来登陆了
|
|
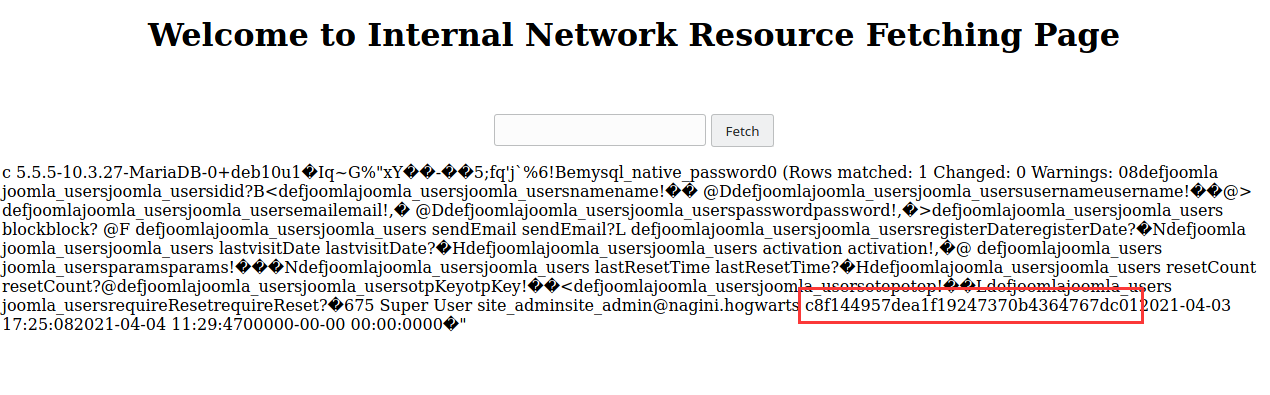
成功修改密码,接下来使用site_admin:密码登录administrator/进下一步操作。
getshell
进入管理界面后尝试写🐎,在媒体库中尝试上传一个php但是失败,翻找一番后发现媒体库可以配置合法文件规则,合法后缀添加php后也还是失败。。。只能找别的思路了,修改模板php文件getshell(默认模板是protostar,如果修改的是另外一个需要设置一下默认模板)
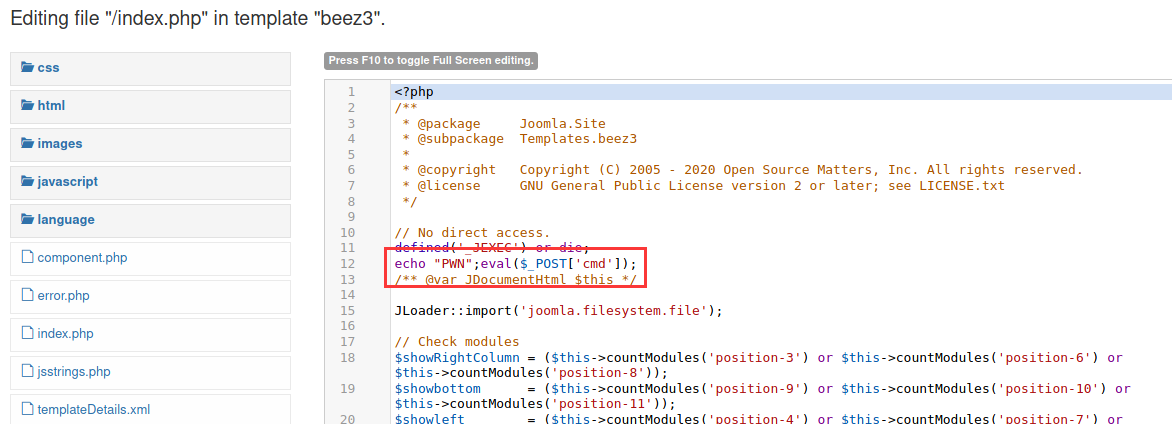
提权
翻文件,在web目录下找到第一个flag文件horcrux1.txt
horcrux_{MzogU2x5dGhFcmlOJ3MgTG9jS0VldCBkRXN0cm9ZZUQgYlkgUm9O}
# horcrux_{3: SlythEriN's LocKEet dEstroYeD bY RoN}
接着翻,home目录下发现两个用户,hermoine用户下有一个suid文件su_cp和无读权限的horcrux2.txt,暂时用不到,另一个用户snape目录下有挺多东西,在.creds.txt读到TG92ZUBsaWxseQ==,解码结果Love@lilly,直接ssh登录。
有了正经用户,接下来就尝试提权,执行sudo -l发现没有sudo指令,结合之前hermoine目录下的可执行文件su_cp,顾名思义,可能是执行sudo cp,猜测这个可能要用来提权,为了保险再找一下suid文件
find / -user root -perm -4000 -print 2>/dev/null
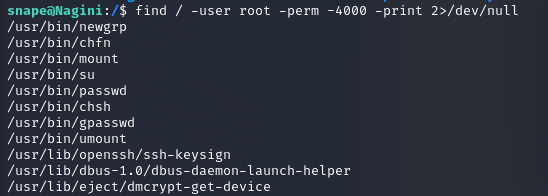
root的suid文件都很正常,那应该还是要依靠hermoine的su_cp,读一下看看有没有什么关键指令,有一个帮助页面,果然和cp的帮助页面一样,应该就是sudo cp。通过这个我们可以实现hermoine的无密码登录(由于权限不足,无法覆盖passwd,伤心)
|
|
此时执行su_cp将公钥拷贝到hermoine的ssh目录
|
|
读取horcrux2.txt
horcrux_{NDogSGVsZ2EgSHVmZmxlcHVmZidzIEN1cCBkZXN0cm95ZWQgYnkgSGVybWlvbmU=}
# horcrux_{4: Helga Hufflepuff's Cup destroyed by Hermione}
后面就是浏览器取证,使用工具firefox_decrypt获得root密码:@Alohomora#123,su登录root获得flag3
